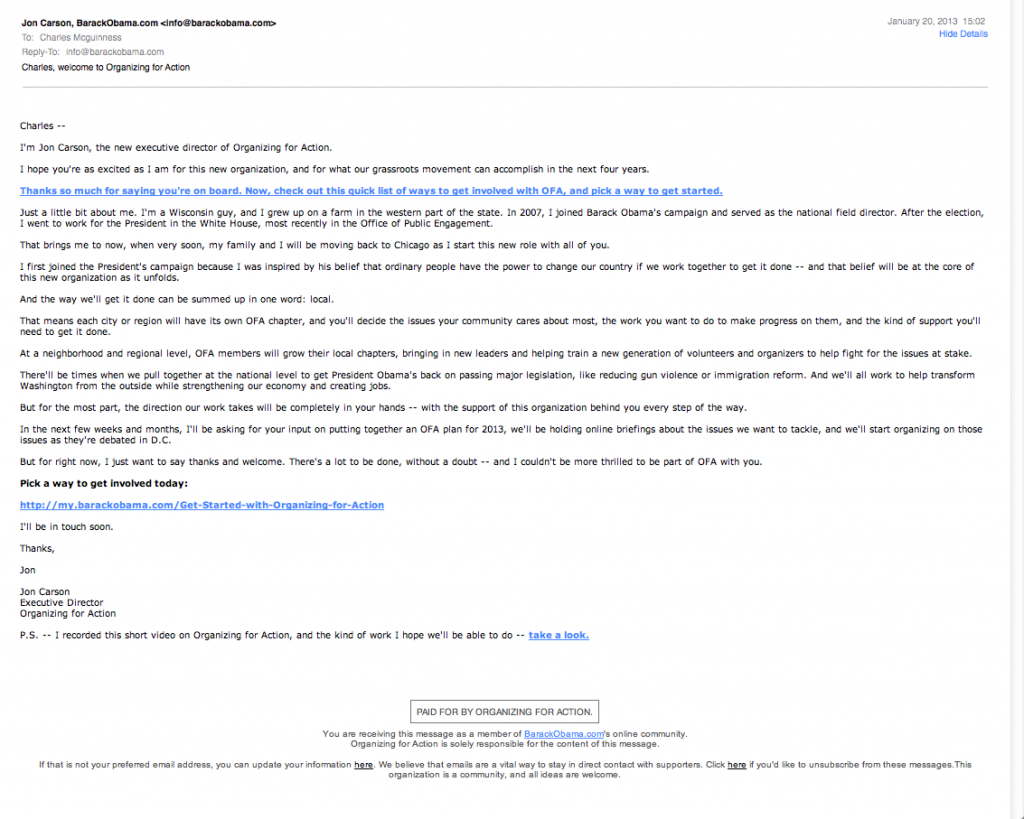
Yesterday I received an email fundraising pitch from Obama’s new Organizing for America:
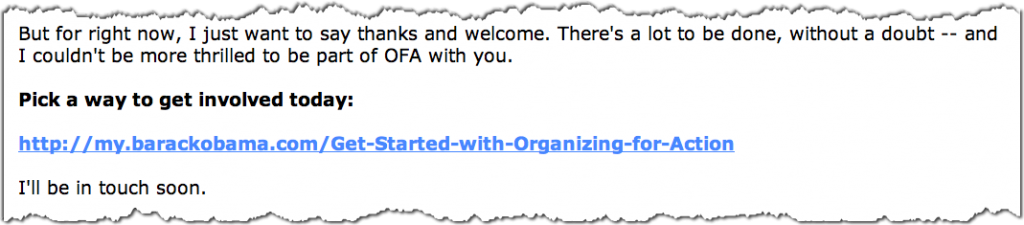
At the bottom of the email is a link to click to :
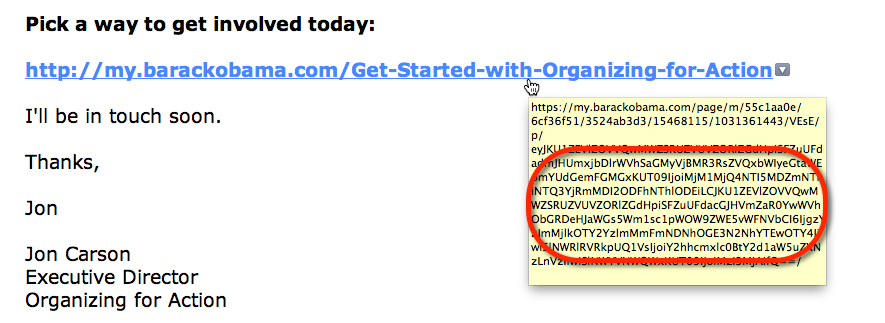
But the text you see is not the actual link that is in the email. That link is really:
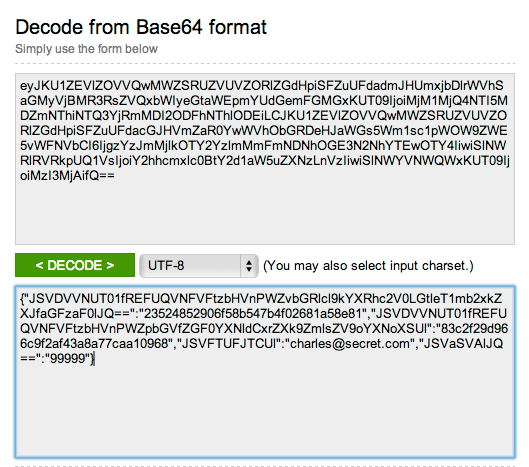
There’s a lot of information in that link, most of which does not appear to be human readable. It turns out that it is encoded using a very common system known as “Base 64”, which is a way to take a bunch of data and put it into a URL like this. But there’s no magic to Base 64, and when you decode it you see:
I’ve replaced my email address (to @secret.com) and zip code (with 99999), however if you are sufficiently energetic you can type in the base 64 text and see what it really is…
Anyone else I share that link with, when they click it, will be taken to the Organizing for Action page and shown my email address and zip code.
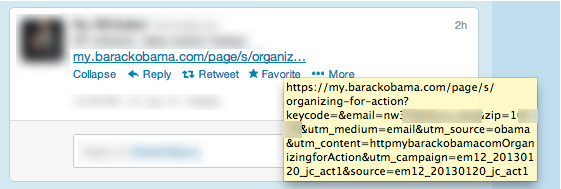
Other people appear to have their email address and zip codes exposed clearly in the links they’ve shared on Twitter:
It’s not a terrible security breach, and I’ve only found about 30 or so people who’ve accidentally done this in the past week. But given that the OFA web site holds credit card information, the leaked data represents two pieces of personally identifiable information that could theoretically be used to assist in identity theft. And if you share such links on Twitter you may find that people who oppose your views find it an opportune time to start up an email conversation you did not solicit…
Regardless of the risk, I am fairly certain (just about all of) the people involved did not intend to publicize their email addresses and home zip codes on Twitter.